Yahallo - Disable Secureboot
What is Yahallo
Refer to The exploit in the dev section to get further information about it.
How does it work
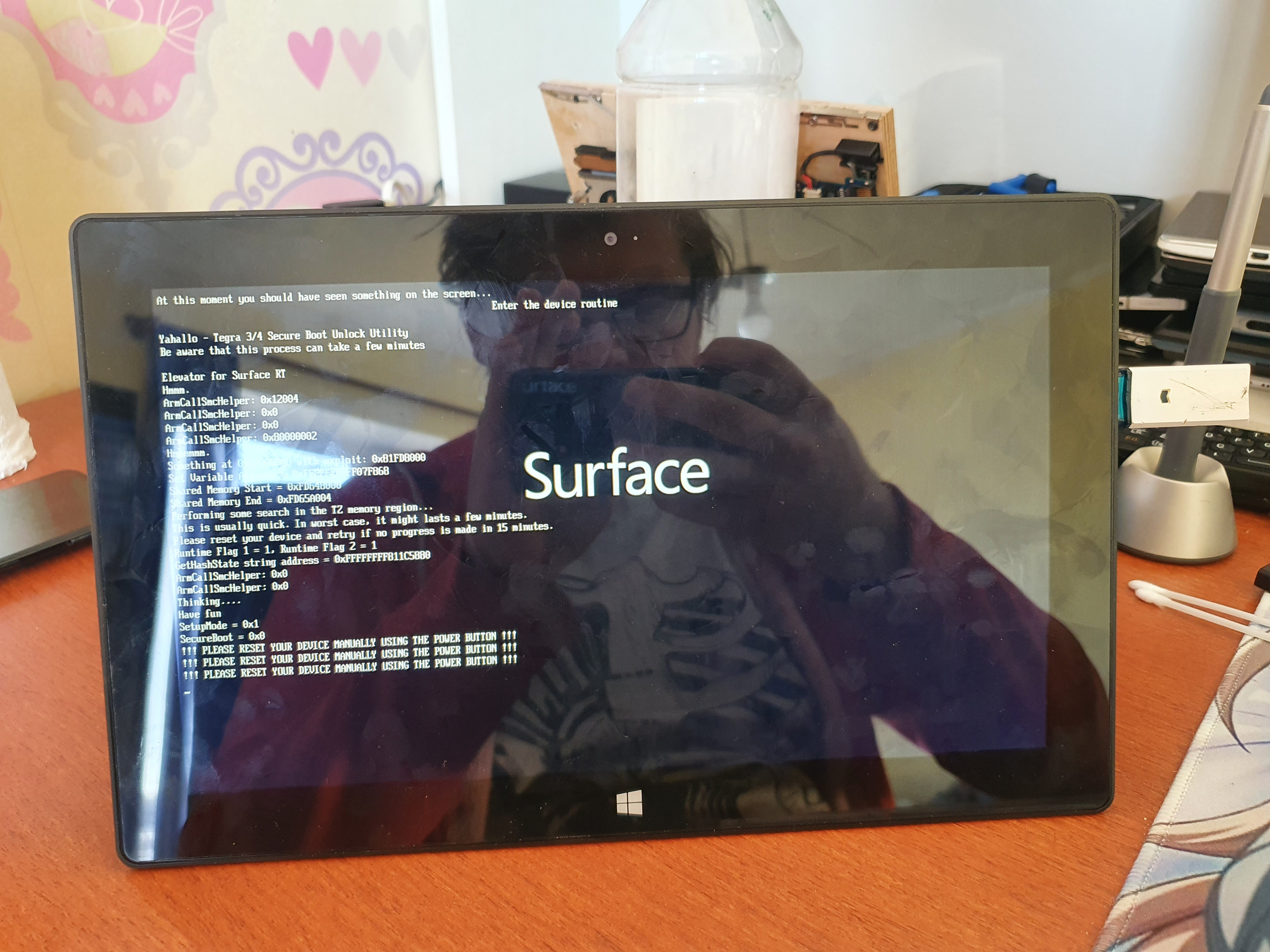
The Exploit starts in App.c. App.c transfers controll to DeviceLut.c It will compare the UEFI version to some entrys in a lookupTable In case of sRT it will apply a display fix first. DeviceLut.c transfers control to Exploit.c
We suggest to only apply this if you need it. In most cases it is not necessary. At the moment you gain no advantage.
https://github.com/NekomimiRouter/yahallo
Executing Yahallo exploit
Quick explanation and multiple options
You can easily disable secure boot by booting the All-in-one Secureboot tool. Just download the ZIP, extract it to your USB and boot it. Select the options with an USB keyboard. For further information how to setup the USB go to the more detailed explanation bellow.
More details can be found in the Secure Boot page and in the All-in-one Secureboot tool page.
Full explanation and single option USB
Prerequisites to start with the process!
Working USB drive formatted as FAT32
Surface RT/2 with 50% or more battery, can be plugged in
Yahallo files to boot from
Windows Boot Manager exploit, this one is important!!!
Prepare the USB drive and format as FAT32, doesn't matter if it's MBR or GPT. In my case I name the drives after their capacity.
Extracting the files, make sure the folder contents are on your USB drive's root directory (example: E:\ [stuff is here])
Once the files are copied over, unplug the drive from your PC and power off your Surface. Once powered off plug in the USB drive and boot from it by pressing power and holding volume down at the same time.
That's it! Exploit has been done and all you have to do is power off your tablet and turn back on. From my case at first it refused to display anything so I suggest leaving it for 5 minutes at most. Since SecureBoot is now disabled you can boot unsigned code like Linux, which is work in progress.
Undo
To re-enable secureboot replace the "Yahallo.efi" file on your USB with the file bellow, make sure the naming is correct.
Enabling secure boot brings you no advantage at all, you only restirct yourself with what you can do.
Last updated