APX Mode (NVIDIA USB Recovery Mode) can be used to run Fusee Gelee or to use Nvidia tools to flash the hardware. https://forum.xda-developers.com/showpost.php?p=77286176&postcount=85
Note - you will need a USB3 port on your development computer.
Power off the SurfaceRT or RT2 (not sleep mode!)
When the device is shut off, plug in a USB type A into the Surface, and a USB type A (or type C depending on your development device) into your development computer.
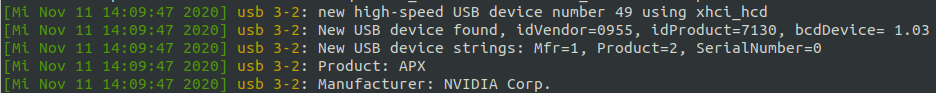
Hold VOL-UP; Press PWR and release it. Release VOL-UP if dmesg -Tw shows:
Once connected in APX mode, you can use NVidia tools or a precompiled Fusee Gelee on your device. Nvflash v2.6 - https://docs.toradex.com/103464-nvfl...ry-toolset.zip NvFlash tool for getting uid - https://web.archive.org/web/20160318...ools-win32.zip
Connect USB - A-to-A cable Write 0x00000002 to 0x7000E450 <- sets bit in PMC-register to indicate to boot to RCM Write 0x00000010 to 0x7000E400 <- reboot This should force reset in RCM Mode
Boot UEFI Shell as normal. use this startup.nsh
Fusee Gelee (translates to Frozen Rocket) is a coldboot launcher. The exploit takes advantage of a USB software stack that is provided inside the BootROM. This stack contains a copy operation that allows for control from attackers. By creating your own USB control request, attacks can use this vulnerability to gain control of the Boot and Power Management Processor (BPMP).
This allows attackers to gain control of the system before any of privilege restrictions are put in place, essentially giving full access to the device. Allowing for the loading of arbitrary code and extraction of secrets.
This vulnerability is completely unpatchable, so the only way to fix this vulnerability is to recall and replace existing SKUs. It affects most of the Tegra devices that were produced before the exploit was published. This includes Surface RT and Surface RT2 and other Tegra3/4 devices.
To use this exploit you need
A payload - a binary file which gets executed
A payload sender - a program which transfers the payload to the device memory.
pyusb
There is a precompiled payload for the Nexus 7 2012 that we can repurpose for the Surface RT (Tegra 3).
The payload provided in this repository has been tested many times, but proceed at your own risk.
You will need to clone this repository into a new directory, including the submodule here:
Once the payload and exploit are downloaded, here are the steps all the way up to flashing an unsigned bootloader:
Connect a USB-A to USB-A cable from your Surface RT to a USB 3.0 port on your host machine.
Boot into APX mode.
Press and hold Volume Up & Power for about 3 seconds
Release the Power button
Release the Volume Up button
lsusb should show a Nvidia device with id 0955:7130
cd into the tegra30_debrick directory
Run the commandsudo ./fusee-launcher/fusee-launcher.py ./payload/uart_payload_n7.bin -V 0955 -P 7130
This will send the uart_payload to the Surface RT, and patch the getSecurityMode function to always return 3, allowing us to use nvflash.
Run the commandsudo ./utils/nvflash_v1.13.87205 --getbct --bct surfacert.bin --configfile ./utils/flash.cfg
This will read the surfacert bct, which is a required input for many nvflash commands.
Finally, we can run arbitrary code using the following command:
sudo ./utils/nvflash_v1.13.87205_miniloader_patched --setbct --bct surfacert.bin --configfile ./utils/flash.cfg --bl u-boot.bin --go
Further tweaking is needed to get a functioning bootloader, with the above steps, and the compiled nvidia fork of u-boot located here (Driver Packages - Cardhu), the webcam light turns on.
Once the L4T R16 u-boot.bin is flashed, you will then need to press and hold the Power button for around 10 seconds to fully power off the tablet. Then you can repeat the above steps to re-attempt flashing.
To get your platform key use this command in the tegra30-debrick directory.sudo ./fusee-launcher/fusee-launcher.py –-tty ./fusee-launcher/dump-sbk-via-usb.bin
Add the -P parameter at the end to specify the product_id if "No TegraRCM device found" is the output. For the Surface RT 1 this is 7130.
This will output a lot of things. Look for the line with hello world, after that line something like this b'e57de3bab6cb499d874d5772cb219f0101042c20'
should show up. Remove the b, the two ' and the last 8 remaining characters. This is your platform key. It is used to encrypt and decrypt the BCT and the firststage bootloader
work in progress.
Looks like UARTA is using the ULPI pins as noted here (https://github.com/u-boot/u-boot/blob/master/arch/arm/mach-tegra/tegra30/pinmux.c#L238) So we know we can setup our UARTA and UARTD on the ULPI pins
#if defined UARTA
/* set pinmux for uart-a (nexus 7) */
reg_write(PINMUX_BASE, PINMUX_AUX_ULPI_DATA0_0, 0b00000110); /* tx */
reg_write(PINMUX_BASE, PINMUX_AUX_ULPI_DATA1_0, 0b00100110); /* rx */
#elif defined UARTD
/* set pinmux for uart-d (ouya */
reg_write(PINMUX_BASE, PINMUX_AUX_ULPI_CLK_0, 0b00000110); /* tx */
reg_write(PINMUX_BASE, PINMUX_AUX_ULPI_DIR_0, 0b00100110); /* rx */
#endif